Operationally equivalent, SocktSpy/16, (for 16-bit Windows 3.1), and SocktSpy/32, (for 32-bit Win'95 an NT), were designed for applications utilizing the WinSock Standard API.
SocktSpy provides tracing capabilities for the following sockets API calls, (WinSock 1.1):
accept() bind() closesocket()
connect() getpeername() getsockname()
getsockopt() htonl() htons()
inet_addr() inet_ntoa() ioctlsocket()
listen() ntohl() ntohs()
recv() recvfrom() select()
send() sendto() setsockopt()
shutdown() socket() gethostbyaddr()
gethostbyname() gethostname() getprotobyname()
getprotobynumber() getservbyname() getservbyport()
WSAASyncGetHostByAddr() WSAAsyncGetHostByName()
WSAAsyncGetProtoByName() WSAAsyncGetProtoByNumber()
WSAAsyncGetServByName() WSAAsyncGetServByPort()
WSAAsyncSelect() WSACancelAsyncRequest()
WSACancelBlockingCall() WSACleanup()
WSAGetLastError() WSAIsBlocking()
WSASetBlockingHook() WSASetLastError()
WSAStartup() WSAUnhookBlockingHook()
In addition, Socket Spy/32 currently, (Dec. 96), supports the following WinSock 2.0 API calls, (including all corresponding callbacks and overlapped operations):
WSAAccept() WSACloseEvent()
WSAConnect() WSACreateEvent()
WSAEnumProtocols() WSAGetOverlappedResult()
WSAHtonl() WSAHtons()
WSANtohl() WSANtohs()
WSARecv() WSARecvFrom()
WSAResetEvent() WSASend()
WSASendTo() WSASetEvent()
WSASocket()
The remaining WinSock 2.0 calls will be added as time permits.
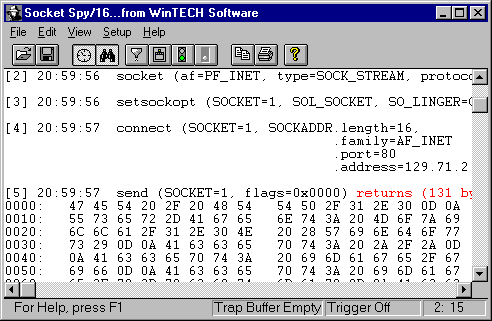
The results of each API call made to the winsock.dll, (wsock32.dll or Ws2_32.dll for 32-bit systems), is captured and displayed to the Spy Window as they occur. Each captured API call contains the arguments passed to the dll as well as any data or error returned as a result of the call. Data transferred through a socket via the recv(), recvfrom(), send(), or sendto() calls may be captured and displayed in its entirety.

Each captured API reference may be displayed in a single-line format or expanded, (Verbose), to display additional argument/return values. SocktSpy may also be configured to only display actual data blocks transferred through a socket between applications, (Data Only Mode).
A filter specification may be applied to SocktSpy to selectively capture particular API commands and/or status return values. Data capture may also be restricted to those API calls associated with a designated socket number.
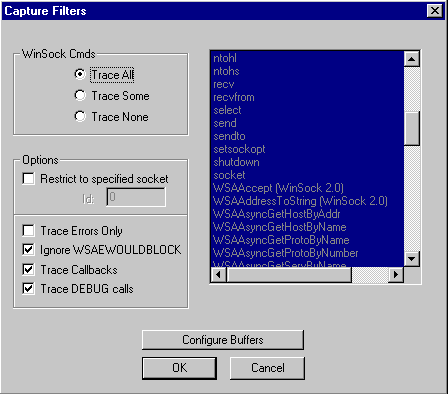
Trace records are maintained in a circular buffer, with newly captured data replacing older data as a monitoring session progresses. SocktSpy maintains a separate and distinct set of trace buffers for trapping communications events based on the occurrence of a defined logic trigger. The trigger may be associated with a given API call, error return value, or byte pattern contained in a send/recv data block.
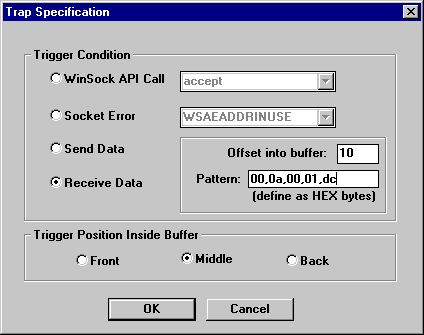
During an active monitoring session, captured API records are compared against the defined trigger, and if a match occurs, trace records are moved from the normal capture buffer to the trap buffer and the trigger is disabled. The trap buffer may be configured to represent the data records immediately prior to the trigger, immediately after the trigger, or surrounding the trigger.
Last Updated: December 29, 1996